
FBI’s ability to see some of the contents of iMessage and collect metadata from WhatsApp in as little as 15 minutes are two of the revelations found on a recently published internal bureau document.
First published last month by Property of the People following a Freedom of Information Act request, the document contains an infographic showing the FBI’s ability to lawfully access secure messaging app content and metadata.
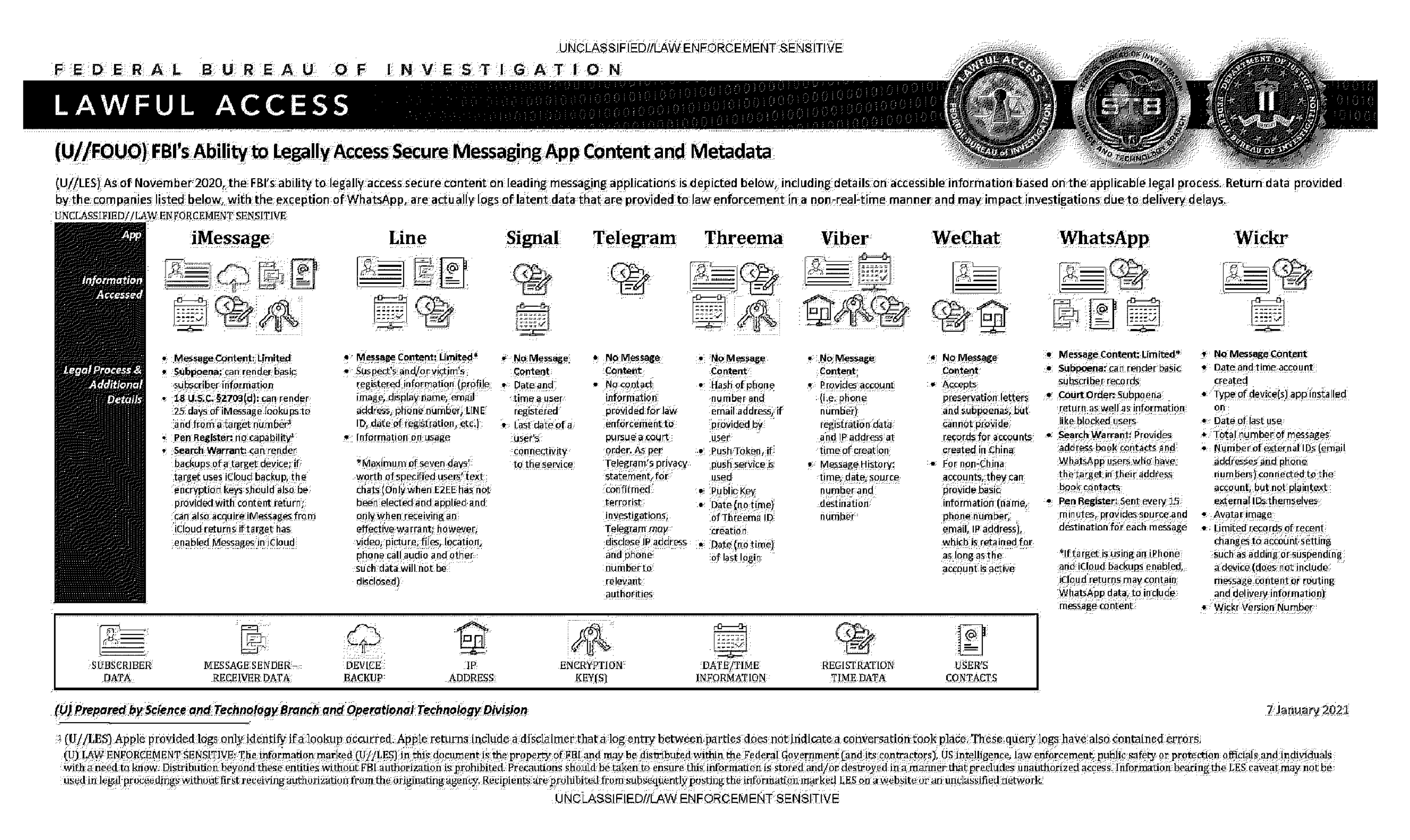
FBI’s collection of messaging and call data has been well-known for years, but the new document reveals the speed and scope with which agents can obtain such information—particularly with Facebook/Meta’s WhatsApp and Apple’s iMessage.
According to the document, WhatsApp provides the FBI with metadata every 15 minutes in response to a “pen register”—a surveillance request that provides the agency with the source and destination of each message for a targeted individual. Other messaging platforms—including iMessage, Signal, Telegram and WeChat—provide logs of latent data, the document said.
document also said the FBI can obtain “limited” content from iMessage. Apple encrypts iMessage, but not the backups in the cloud—unlike WhatsApp, which started offering encryption for backups in September.

“Search warrant can render backups of a targeted device,” the FBI document said. “If target uses iCloud backup, the encryption keys should also be provided with content return; can also acquire iMessages from iCloud returns if target has enabled iMessages in iCloud.”
FBI can also still see the contents of backed-up WhatsApp messages if they are unencrypted, which is still the default setting.
Other platforms included in the FBI document include Signal, Telegram, and WeChat—none of which provide message contents to law enforcement. Chinese-owned WeChat accepts subpoenas for metadata, but doesn’t provide records for accounts created in China, according to the FBI.
“For non-China accounts, they can provide basic information (name, phone number, email, IP address), which is retained for as long as the account is active,” the FBI document said.

extent to which the FBI collects metadata isn’t clear. Facebook’s transparency center says the company received 63,657 law enforcement requests in the United States from January to June 2021, but doesn’t distill the data further to show what agencies are making the requests.
Apple did not respond to an inquiry from Pezou. After the document was published Nov. 19, Facebook/Meta told the Rolling Stone that the FBI document “illustrates what we’ve been saying—that law enforcement doesn’t need to break end-to-end encryption to successfully investigate crimes.”
FBI has long argued that end-to-end encrypted chat platforms hinder its investigations on a number of issues, from ransomware to child pornography and domestic terrorism.

“I can’t overstate the impact of default encryption and the role it’s playing, including on terrorism,” FBI director Christopher Wray said at a September congressional hearing.
“ information that will allow us to separate the wheat from the chaff, in terms of social media, is being able to—with lawful process—get access to those communications, where most of the meaningful discussions of the violence is occurring.”
During a Dec. 3 livestream, technologists for the Freedom of the Press Foundation agreed with Facebook: FBI’s access to messaging metadata should be enough for agents to be able to conduct investigations.
Whereas law enforcement could only usually collect a few data points on traditional calls—such as the phone numbers involved in the conversation—they can now collect troves of information on IP addresses, the port and protocols used, date, time and location, said the Freedom of the Press Foundation’s chief information security officer, Harlo Holmes.
“Facebook is pretty much saying, ‘You have a couple of tools if you know how to use them,’” said Holmes. “Use data acquired via WhatsApp to pivot onto another legal request.”
Pezou : FBI Can Collect WhatsApp Metadata in 15 Minutes: Document